What is Policy-Based Routing and why to use it?
Policy-based routing (PBR) is a technique used to make routing decisions based on policies set by the network administrator. When a router receives a packet it normally decides where to forward it based on the destination address in the packet, which is then used to look up an entry in a routing table. However, in some cases, there may be a need to forward the packet based on other criteria. For example, a network administrator might want to forward a packet based on the source address, not the destination address.
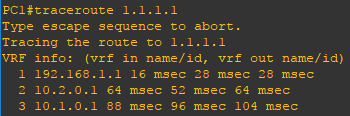
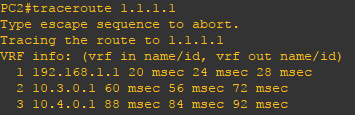
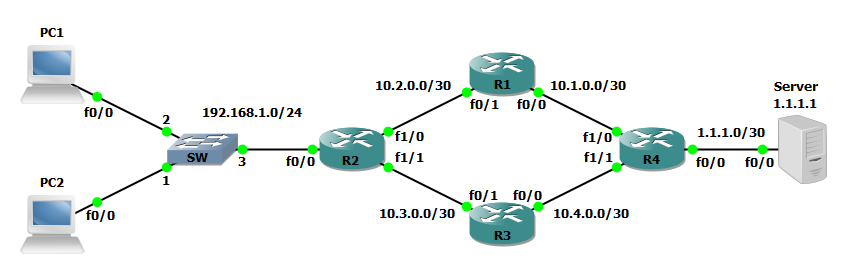
In the network below there are a total of four routers, two end-user computers and a server. In real world deployments a network could have dozens or hundreds of routers or devices depending on the scale of the network. Static routes are deployed to establish full network connectivity between the end-user computers and the server. Additionally route-maps and route policies are deployed to route PC1 over the network path of R2 to R1 to R4 and PC2 over the network path of R2 to R3 to R4 to reach the remote server.
Steps to configure Policy-Based Routing
Step 1: Configure all applicable router interfaces.
R2(config)#interface FastEthernet0/0 R2(config-if)#ip address 192.168.1.1 255.255.255.0 ! R2(config)#interface FastEthernet1/0 R2(config-if)#ip address 10.2.0.2 255.255.255.252 ! R2(config)#interface FastEthernet1/1 R2(config-if)#ip address 10.3.0.2 255.255.255.252
Step 2: Configure static routes to all remote networks unknown to the router. This must include a route to the network the remote computer resides as well as any remote networks between the source router and destination not directly connected to the source router.
R2(config)#ip route 1.1.1.0 255.255.255.252 10.2.0.1 R2(config)#ip route 1.1.1.0 255.255.255.252 10.3.0.1 R2(config)#ip route 10.1.0.0 255.255.255.252 10.2.0.1 R2(config)#ip route 10.4.0.0 255.255.255.252 10.3.0.1
Step 3: Repeat the same steps on all remaining routers with the applicable interface and routing configurations.
Step 4: Create access-list to target PC1 and PC2, respectively, so when they try to communicate with 1.1.1.1 the route-map is applicable.
R2(config)#access-list 101 permit ip host 192.168.1.11 host 1.1.1.1 R2(config)#access-list 102 permit ip host 192.168.1.12 host 1.1.1.1
Step 5: Configure route-maps that make use of the access-list and specify a specific next-hop.
R2(config)#route-map pbr permit 10 R2(config-route-map)#match ip address 101 R2(config-route-map)#set ip next-hop 10.2.0.1 ! R2(config)#route-map pbr permit 20 R2(config-route-map)#match ip address 102 R2(config-route-map)#set ip next-hop 10.3.0.1 ! R2(config)#interface FastEthernet0/0 R2(config-if)#ip policy route-map pbr
TIP: You can also use IP SLA with route-maps in order to track and failover a route. In this scenario you can avoid specifying a single next-hop in the route-map and instead specify a primary and backup next-hop. The command would look like set ip next-hop 10.2.0.1 10.3.0.1. Without using IP SLA the secondary next-hop will never become active. You can read more about how to make use of Router Failover using IP SLA here.
Verify the configuration
Now that the configuration is finished lets verify our routes. Using the show ip route and traceroute commands you can verify the expected routes in the routing table and verify the network path (route) used. Use the ping command to verify connectivity.