What is debugging and why to use it?
Steps to configure debugging safely
R1#terminal length 0 R1(config)#service sequence-numbers R1(config)#service timestamps debug datetime localtime msec R1(config)#logging buffered 10000000 debug R1(config)#no logging console R1(config)#no logging monitor R1(config)#default logging rate-limit R1(config)#default logging queue-limit R1(config)#voice iec syslog
Step 2: In this example we are simululating a VPN problem. We will configure a site-to-site IPsec VPN but configure R2 with a mismatched crypto password.
R2(config)#no crypto isakmp key vpnpasswordhere address 1.1.1.1 R2(config)#! R2(config)#crypto isakmp key wrongvpnpassword address 1.1.1.1
Step 3: Enable session capture to txt file in the putty terminal program.
Step 4: Clear the router’s logs before enable debugging to get a clearer view of what is happening.
R1#clear logging system
Step 4: Enable debugging using one or more debug command then wait for the issue to occur. When finished issue the no debug command.
R1#debug crypto isakmp ! R1#no debug crypto isakmp
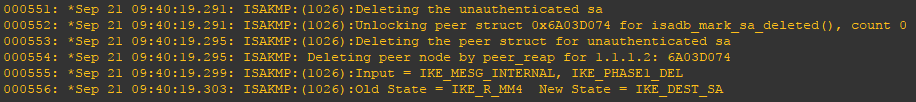
Step 5: show the local log output and review findings.
R1#show logging
Step 6: In reviewing the loging we can see the below output where “Deleting the unauthenticated sa” and “Deleting the peer struct for unauthenticated sa”. We can further observe in the logging “Death by retransmission P1” indicating the VPN is failing in phase 1 and there is no mention of phase 2.